Autopsy 4.17 is out with a long list of changes. Let’s cover a few new things that were introduced. You’ll notice a common theme that these were incrementally released with future evolutions in the works. You can see the full list of changes here and download the latest version from here.
In this post, we’ll cover:
Data Source Summary
iOS Forensics using iLEAPP
HEIC Pictures and Picture Analyzer Module
Data Source Summary
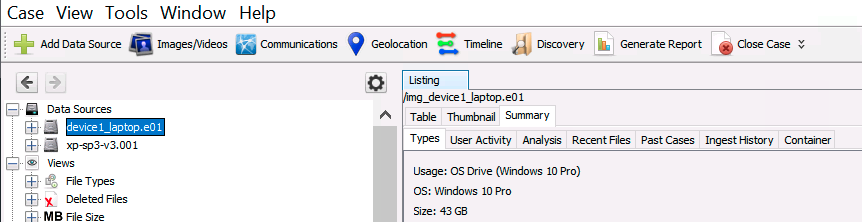
We re-organized and added more information to the Data Source Summary panel that was introduced last year. The goal of the panel is to give the examiner a quick overview of the data source to help make prioritization decisions or to help direct the examination.
You can get to the panel in a few ways, but the easiest is to select the data source and choose the “Summary” tab on the right.
For each data source, you’ll see tabs for the following:
Types: Shows basic information such as the number of files, file types, OS Type, etc. for the data source. The goal is to get some basic understanding of size and types of files.
User Activity: Shows the 10 most recent programs launched, domains visited, web searches, USB devices attached, and account types used. The goal is to get an idea about what kinds of high-level things the user does with the device.
Analysis: Highlights the hashsets, keyword lists, and Interesting Item sets that had hits on the data source.
Recent Files: Shows the 10 most recent files opened by common apps or downloaded by web browsers. The goal is to get more specific on what files were interesting to the user.
Past Cases: This will show which cases had the same files or artifacts as this data source AND those cases marked the item as notable. This relies on data from the Central Repository.
Ingest History: Shows you what ingest modules were run on the data source.
Container: Provides overview information about the E01 or raw image file.
If there is anything else you’d like to see here, then please let us know. The next release will add panels to show a mini-timeline of activity and cities that the geolocation data is associated with.
iOS Forensics With iLEAPP
There is a new “iOS Analyzer (iLEAPP)” ingest module that wraps the iLEAPP program from Alexis Brignoni, Yogesh Khatri, and others. This effort is a work in progress and this release parses a limited number of the wide variety of results that iLEAPP can produce. The next release will add the rest of the artifacts, support for disk images, and aLEAPP for Androids!
Inputs
For this release, the input to iLEAPP needs to be a tar file. If you add the tar file as a logical file to Autopsy and it is in the root folder, then the iOS Analyzer module will detect it and run iLEAPP on it.
For example:
Your data source is at c:imagescase123phone1.tar
You add the c:imagescase123phone1.tar file as a logical file into Autopsy.
Artifacts
This release focuses on artifacts that Autopsy already had support for. Such as web browsers, Wifi, installed programs, programs run, etc.
Autopsy gets them by running iLEAPP to produce TSV files. Autopsy has a configuration file that maps the files and columns to an Autopsy artifact. As iLEAPP adds new modules, all someone needs to do is update this XML file. No code is required!
Next Release
In addition to mapping more artifacts, the next release will also allow you to analyze disk images or logical images that are not in a TAR file. iLEAPP added a feature to output the list of files it needs. We’ve used that list to query Autopsy’s file manager for them, export them to disk, and then run iLEAPP on them.
HEIC Support and Picture Analyzer Module
There is a new module named “Picture Analyzer”. It will be the central module focused on image and video-based analysis. The EXIF module functionality has been moved to this module and support for HEIC pictures was added. HEIC files are now converted to JPG files and added as children of the HEIC picture.
Try it Out
You can download the latest version from here.
The post Autopsy 4.17 Highlights (Summary, iLEAPP, & HEIC) appeared first on Autopsy.